In today’s digital era, it’s nearly impossible to read the news without seeing a headline about a significant cyber breach. The most recent incident involves Change Healthcare, a unit of UnitedHealth Group, which fell victim to a sophisticated cyberattack by the notorious group ALPHV/Blackcat. This event serves as a crucial learning opportunity for organizations worldwide. Let’s explore the details of this breach and discuss proactive strategies to safeguard your company from becoming the next headline.
Understanding the Change Healthcare Cyberattack
A recent article by CRN, “5 Things To Know On The UnitedHealth Optum Cyberattack,” offers an insightful summary of this significant cybersecurity incident. Originating from what’s believed to be “nation-state” hackers, the attack had a profound impact on the U.S. healthcare billing system. The disruption involved the shutdown of crucial IT systems and services under Change Healthcare, creating a domino effect of complications for healthcare clinics, billing companies, and pharmacies nationwide.
BleepingComputer reported that the ALPHV/Blackcat ransomware gang claims to have exfiltrated a staggering 6TB of sensitive data from Change Healthcare. This breach, involving personal and medical information, has wide-reaching implications for countless individuals linked to the healthcare sector.
ALPHV/Blackcat: A New Wave of Cyber Threats
ALPHV ransomware is notably the first major ransomware developed using Rust, a language known for its efficiency and security. Its advanced techniques in privilege escalation and complex encryption methods (AES or ChaCha20) signify a significant evolution in ransomware technology. For a more in-depth understanding, SecurityScorecard‘s entire article is an excellent resource.
This ransomware employs various tactics:
- Reconnaissance through phishing.
- Compromised accounts for network access.
- Credential theft from password stores.
- Kerberos ticket exploitation for domain access.
- Using the Evilginx2 framework to capture MFA, login credentials, and session cookies.
How They Possibly Gained Access:
- Flaw Exposed: ConnectWise’s Critical Vulnerability- On February 19, 2024, ConnectWise issued a crucial security advisory for ScreenConnect version 23.9.8, revealing two significant vulnerabilities. These weaknesses could open the door to cyber threats that put your network at risk.
- Vulnerability Exploited: A Closer Look – Experts believe threat actors have exploited these flaws, as detailed in an insightful Huntress analysis and this enlightening video: Watch Here.
- Inside the Network: The Danger of Lateral Movement – Attackers gain complete access to a company’s network with this breach. This enables them to easily navigate the network, deploy tools, and access critical data, laying the groundwork for further exploitation.
- Taking Control: The Threat Actors’ Playbook – Once inside, these attackers use every tool at their disposal to extract valuable information. From executing advanced PowerShell commands to injecting shellcode into memory, their tactics are varied and sophisticated, aimed at crippling the company’s digital infrastructure.
- Data Theft in Action: The Exfiltration Strategy – Armed with their arsenal, these threat actors systematically steal sensitive information, undermining the company’s data and infrastructure security.
- Devastating Impact: Encryption and Disruption – The culmination of these attacks often includes encrypting files and displaying ransom demands, drastically disrupting business operations. These actors intensify their assault by shutting down essential services and erasing recovery options like volume shadow copies. Tactics like rebooting systems in safe mode before encryption, a hallmark of variants like Sphynx, amplify the devastation.
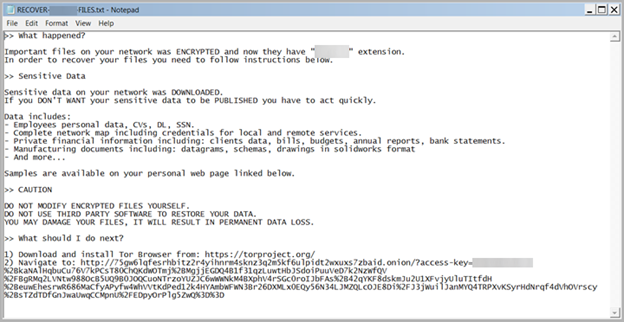
Source: Trend Micro
Mitigating Cyber Threats: A Practical Guide
The alarming statistic from IT Governance USA shows that over 30 billion records have been breached this year, with 93% of affected companies experiencing data theft. To combat this type of ransomware, it’s crucial to adopt a multi-faceted cybersecurity approach:
- Regular System Updates and Patch Management: Keep all systems and software up-to-date with the latest security patches. This helps close vulnerabilities that threat actors could exploit.
- Employee Education and Awareness: Train employees to recognize the signs of phishing attacks, one of the standard methods used by ransomware for initial penetration. Regular awareness programs can significantly reduce the risk of employees inadvertently compromising the network.
- Advanced Threat Detection Systems: Implement security solutions that can detect and respond to sophisticated malware, including behavior analysis tools and advanced threat detection systems that identify ransomware activity anomalies.
- Robust Data Backup and Recovery Plan: Maintain regular backups of critical data and ensure that these backups are stored securely, ideally in an offsite or cloud-based service. This minimizes the damage in case of a successful ransomware attack.
- Network Segmentation: Segment your network to limit the spread of ransomware if it penetrates your defenses. By isolating different parts of your network, you can prevent widespread compromise.
- Multi-Factor Authentication (MFA): Implement MFA for all system and application access to add an extra layer of security, making it more difficult for attackers to gain access even if they obtain user credentials.
By focusing on these critical areas, organizations can better protect themselves against the specific threats of sophisticated ransomware like ALPHV/Blackcat.
Elevate Your Cybersecurity Posture
At Alchemy Technology Group, we understand that cybersecurity technologies are not one-size-fits-all. Our partnership with over 200 leading technology vendors enables us to offer tailored solutions that align with your needs. Whether enhancing your current team with our Cybersecurity Advisory services or leveraging our comprehensive Security Assessment, we’re here to fortify your defense against cyber threats.
Alchemy’s Security Assessment
Alchemy Technology Group’s Security Assessment service comprehensively analyzes an organization’s cybersecurity posture. The process involves identifying and evaluating potential risks and vulnerabilities across technology, processes, and people. Utilizing industry-leading standards like NIST and SANS Institute, Alchemy’s assessment aims to enhance cybersecurity measures and minimize threats. Their methodology includes risk profiling, strategic resource allocation for risk mitigation, and establishing controls aligned with industry standards. The service will strengthen the security landscape of the businesses, providing tailored recommendations for improved security and compliance.
> Book Your Security Assessment Today
Alchemy’s Cybersecurity Advisory Solutions
Alchemy’s Cybersecurity Advisory services provide expert, strategic cybersecurity guidance to organizations. This service is ideal for businesses with limited cybersecurity leadership resources. It offers strategic cybersecurity leadership, customized security roadmaps, continuous risk assessment and mitigation, compliance expertise, comprehensive penetration testing, incident response, business continuity planning, and cost-effective scalability. This solution will offer flexibility and specialized knowledge to protect against evolving cyber threats and adapt to security challenges.
Staying Ahead in the Cybersecurity Game
In conclusion, the cyberattack on Change Healthcare is a stark reminder of the evolving landscape of cyber threats. In this digital age, staying informed and proactive is crucial for any organization. By understanding the nature of these threats and implementing robust security strategies, you can significantly reduce your risk and ensure that your organization remains resilient in the face of cyber challenges. Remember, in cybersecurity, being reactive is no longer an option; being proactive is the key to safeguarding your digital frontier.


